Every successful interview starts with knowing what to expect. In this blog, we’ll take you through the top Network Analysis and Visualization interview questions, breaking them down with expert tips to help you deliver impactful answers. Step into your next interview fully prepared and ready to succeed.
Questions Asked in Network Analysis and Visualization Interview
Q 1. Explain the difference between directed and undirected graphs.
The core difference between directed and undirected graphs lies in the nature of the connections, or edges, between nodes. Imagine a social network:
- Undirected graphs represent relationships where the connection is reciprocal. If person A is friends with person B, then person B is also friends with person A. The edge between them is represented without an arrow, indicating symmetry.
- Directed graphs, or digraphs, represent relationships with directionality. If person A follows person B on Twitter, the connection is only one-way; B doesn’t necessarily follow A back. The edge from A to B would have an arrow, indicating the direction of the relationship.
Think of it like a road network: an undirected graph represents a two-way street, while a directed graph can represent a one-way street.
Formally, in an undirected graph, the edge (A, B) is equivalent to (B, A). In a directed graph, (A, B) is distinct from (B, A).
Q 2. Describe various graph traversal algorithms (BFS, DFS) and their applications.
Graph traversal algorithms explore all the nodes and edges in a graph. Two fundamental algorithms are Breadth-First Search (BFS) and Depth-First Search (DFS):
- Breadth-First Search (BFS): BFS explores a graph level by level. Imagine you’re searching for someone in a crowd; you’d check everyone around you first, then their neighbors, and so on. It uses a queue data structure. BFS is excellent for finding the shortest path in unweighted graphs.
- Depth-First Search (DFS): DFS explores a graph by going as deep as possible along each branch before backtracking. Think of it like exploring a maze; you’d follow one path until it hits a dead end, then backtrack and try another. It uses a stack (or recursion). DFS is useful for finding cycles in a graph or traversing tree-like structures.
Applications:
- BFS: Finding the shortest path in a network (GPS navigation), finding connected components in a graph, social network analysis (finding people within a certain distance).
- DFS: Topological sorting (ordering tasks based on dependencies), cycle detection in a graph, finding strongly connected components, web crawlers.
Q 3. What are the strengths and weaknesses of different graph visualization techniques (e.g., force-directed, hierarchical)?
Several techniques visualize graphs, each with strengths and weaknesses:
- Force-directed layouts: These algorithms simulate physical forces (repulsion and attraction) between nodes to arrange them. Think of magnets pushing and pulling each other. They are good at revealing clusters and community structure but can be slow for large graphs and can sometimes produce cluttered visualizations.
- Hierarchical layouts: These layouts arrange nodes in a hierarchical tree-like structure, often based on a defined parent-child relationship. They are excellent for showing hierarchical data (e.g., organizational charts) but are not suitable for non-hierarchical data.
- Circular layouts: Arrange nodes along a circle. Simple to understand and suitable for small graphs with uniform relations. Less effective for large graphs or those with community structures.
- Matrix layouts: Represent the graph using adjacency matrix. Useful for highlighting the connection density. However, it is difficult to visualize for larger graphs.
The best visualization technique depends heavily on the graph’s structure and the insights you aim to extract. For instance, a force-directed layout might be preferable for exploring community structure in a social network, while a hierarchical layout would be more suitable for visualizing a file system.
Q 4. How do you handle missing data in network analysis?
Missing data is a common challenge in network analysis. The approach to handling it depends on the type and amount of missingness:
- Imputation: This involves filling in missing values based on existing data. Methods include mean/median imputation, k-Nearest Neighbors (k-NN) imputation, or model-based imputation. However, imputation can bias results if not done carefully.
- Deletion: Removing nodes or edges with missing data is a simple but potentially problematic approach, particularly if a large proportion of data is missing. This can significantly alter the structure and analysis of the network.
- Multiple imputation: Create multiple plausible imputed datasets and analyze them separately, combining results for more robust conclusions. This is a sophisticated approach but computationally intensive.
- Sensitivity analysis: Assessing how the results vary under different imputation or deletion strategies can help assess the impact of missing data on the analysis.
The best method depends on the specific context and the nature of missingness. It’s crucial to document the strategy used and acknowledge the potential limitations it might introduce.
Q 5. Explain the concept of centrality measures (degree, betweenness, closeness, eigenvector) and their interpretations.
Centrality measures quantify the importance of nodes within a network. Several key measures exist:
- Degree Centrality: The number of direct connections a node has. A highly connected node has high degree centrality. Think of a popular person on social media with many followers—high degree centrality.
- Betweenness Centrality: Measures how often a node lies on the shortest paths between other nodes. Nodes with high betweenness centrality act as bridges, connecting otherwise distant parts of the network. Think of an influential person who connects disparate groups.
- Closeness Centrality: Measures the average distance of a node to all other reachable nodes. Nodes with high closeness centrality have short paths to all other nodes and can quickly spread information or influence.
- Eigenvector Centrality: A node’s importance is determined by the importance of its neighbors. A node connected to many important nodes has high eigenvector centrality, even if its degree is not exceptionally high. Think of a person with a few highly influential friends.
Interpreting centrality measures requires considering the network’s context and the specific measure used. For example, a node might have high degree centrality but low betweenness centrality.
Q 6. What are community detection algorithms and how do they work?
Community detection algorithms aim to identify groups or clusters of densely interconnected nodes within a larger network. These algorithms work by trying to optimize different criteria, such as maximizing the density of edges within communities and minimizing edges between them. Common algorithms include:
- Louvain algorithm: A greedy algorithm that iteratively refines community assignments to optimize modularity—a measure of the network’s community structure.
- Girvan-Newman algorithm: This algorithm iteratively removes edges with the highest betweenness centrality, thus separating communities.
- Label Propagation algorithm: A simple and fast algorithm that iteratively propagates community labels through the network.
These algorithms produce different results depending on the network structure and their parameter settings. Choosing the appropriate algorithm requires understanding their strengths and limitations and potentially testing multiple algorithms.
Q 7. How do you identify and handle outliers in network data?
Outliers in network data can represent nodes or edges that deviate significantly from the overall network structure. Identifying and handling them requires a multifaceted approach:
- Visual inspection: Examining visualizations (e.g., degree distributions) can reveal nodes with unusually high or low connectivity.
- Statistical measures: Calculate statistical measures such as z-scores or modified z-scores based on degree centrality or other relevant metrics to identify nodes that fall outside of a defined range.
- Community detection: Nodes that consistently belong to no community or are isolated might be outliers.
Handling outliers depends on their nature and the research question. Options include:
- Removal: Outliers can be removed if they are deemed spurious or irrelevant to the study’s focus, but this should be justified and its impact assessed.
- Further investigation: Investigate the outlier’s characteristics to understand the reasons for their unusual behavior. They may represent important aspects of the system that warrant closer attention.
- Robust methods: Use robust analytical techniques that are less sensitive to outliers, such as median-based statistics instead of mean-based ones.
Careful consideration is needed when handling outliers as they can contain important information about the network structure.
Q 8. Explain different types of network models (e.g., Erdős–Rényi, Barabási–Albert).
Network models are mathematical representations of relationships between entities. Different models capture different aspects of these relationships. Two fundamental examples are the Erdős–Rényi (ER) and Barabási–Albert (BA) models.
Erdős–Rényi (ER) Model: This is a random graph model. Imagine throwing darts randomly at a dartboard representing nodes. Each dart represents a possible connection. The probability of connection between any two nodes is constant and independent of other connections. This creates networks with a relatively uniform structure. ER models are useful for studying the properties of completely random networks, serving as a baseline for comparison with real-world networks.
Barabási–Albert (BA) Model: This is a preferential attachment model. It generates networks with a scale-free structure, meaning a small number of nodes have a disproportionately large number of connections (hubs). Think of a social network where popular people tend to attract more connections. The BA model simulates this by having new nodes preferentially link to already well-connected nodes. This better reflects the structure of many real-world networks, like the internet or social networks.
Other models exist, such as the Watts-Strogatz model (small-world networks), which balance regularity and randomness. The choice of model depends heavily on the network being studied and the questions being asked.
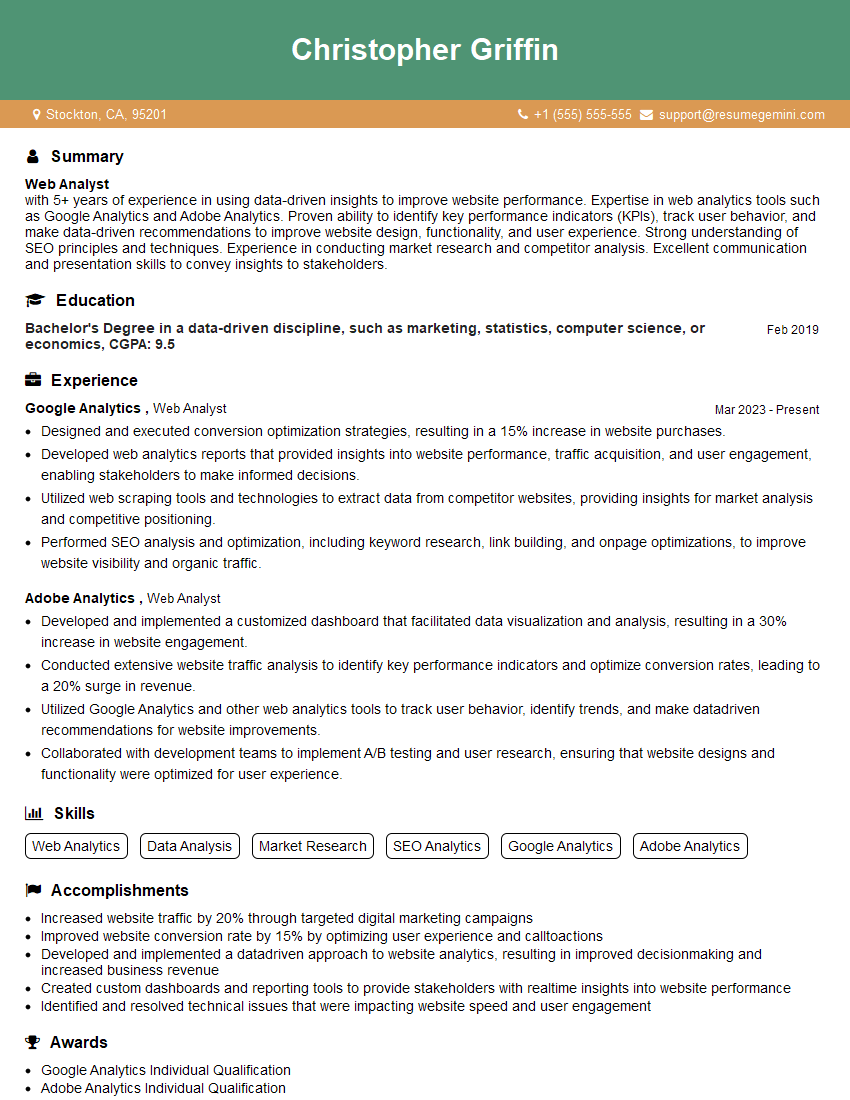
Q 9. Describe your experience with network analysis software (e.g., Gephi, Cytoscape, NetworkX).
I have extensive experience with several network analysis software packages. My proficiency spans from data import and preprocessing to complex analysis and visualization.
Gephi: I’ve used Gephi extensively for its powerful visualization capabilities, particularly for exploring large, complex networks. I’ve leveraged its layout algorithms (ForceAtlas2, Fruchterman-Reingold) to uncover community structures and identify key players. For example, in a project analyzing a citation network, Gephi helped visualize clusters of highly cited papers, revealing influential research areas.
Cytoscape: Cytoscape is my go-to for integrating network analysis with biological data. Its plugin architecture allows for a vast range of analyses, from pathway enrichment analysis to network motif detection. I used Cytoscape to analyze protein-protein interaction networks, integrating gene expression data to identify key regulators of cellular processes.
NetworkX: NetworkX is my preferred choice for Python-based analysis. It provides a robust and versatile library for creating, manipulating, and analyzing networks programmatically. I’ve used it to perform various calculations, including centrality measures, community detection, and pathfinding algorithms, all automated within larger workflows.
My experience extends beyond these specific tools; I’m comfortable adapting to new software as needed, guided by the specific requirements of the project.
Q 10. How do you assess the statistical significance of network properties?
Assessing the statistical significance of network properties is crucial to avoid drawing spurious conclusions. We typically use several approaches, often in combination.
Permutation Tests: These are non-parametric tests where we randomly shuffle the network edges and recalculate the property of interest (e.g., clustering coefficient, degree distribution). If the observed value is significantly different from the distribution of values obtained through randomization, we reject the null hypothesis that the observed property is due to chance.
Comparison to Null Models: We compare the network’s properties to those of null models, such as ER or configuration models. These null models control for certain network features (e.g., degree distribution) while removing others. Significant deviations from the null model suggest non-random processes shaped the network.
Confidence Intervals: Calculating confidence intervals around network metrics provides a measure of uncertainty. A narrow confidence interval indicates greater confidence in the estimated value.
The choice of method depends on the specific network property and the available data. It’s often essential to employ multiple techniques to strengthen the conclusions.
Q 11. Explain the concept of network robustness and how to measure it.
Network robustness refers to a network’s ability to maintain its functionality despite disruptions or attacks (e.g., node or edge failures). Measuring robustness involves assessing how the network structure and performance change under stress.
Node/Edge Removal: A common approach is to iteratively remove nodes or edges and measure the impact on key network properties like connectedness, diameter, or average shortest path length. The rate at which these properties degrade indicates the network’s robustness.
Centrality Measures: Nodes with high centrality scores (e.g., degree centrality, betweenness centrality) are critical to network function. Removing these nodes causes more significant disruption, highlighting vulnerabilities.
Resilience Metrics: These metrics quantify the impact of disruptions. For example, the size of the largest connected component after node/edge removal can reflect the overall system resilience.
For example, in power grid analysis, robustness assessment helps identify critical infrastructure components to ensure reliable electricity supply. In social networks, it can reveal influential actors whose removal would severely impact information dissemination.
Q 12. How do you visualize large networks efficiently?
Visualizing large networks efficiently requires a multi-pronged approach combining algorithmic and visual techniques.
Sampling: Instead of visualizing the entire network, we can visualize a representative sample. This reduces computational burden while retaining essential information. Careful sampling techniques are crucial to avoid bias.
Hierarchical Representations: We can use hierarchical layouts to group similar nodes, reducing visual clutter. Community detection algorithms can identify these groups.
Edge Bundling: This technique groups parallel or similar edges into bundles, simplifying the visualization while maintaining information about the overall connectivity patterns.
Interactive Visualizations: Interactive tools allow users to zoom, pan, filter, and highlight specific parts of the network, offering greater control and understanding.
Focus+Context Techniques: These display a detailed view of a specific part of the network within the context of the larger structure.
The best approach depends on the network’s size, structure, and the specific insights being sought. Combining multiple techniques often yields the most effective visualization.
Q 13. What are the ethical considerations in network analysis?
Ethical considerations in network analysis are paramount. The potential for misuse necessitates careful attention to privacy, bias, and transparency.
Privacy: Network data often contains sensitive information about individuals or organizations. Anonymization or aggregation techniques are crucial to protect privacy and prevent re-identification.
Bias: Network analysis can perpetuate or amplify existing biases present in the data. Careful consideration of data collection methods and analysis techniques is necessary to mitigate bias and ensure fair representation.
Transparency: The methods used for data collection, preprocessing, analysis, and visualization should be clearly documented and reproducible. This ensures accountability and allows for critical evaluation of results.
Informed Consent: If data involves human subjects, informed consent is crucial. Participants should be fully aware of how their data will be used and protected.
Ignoring these ethical considerations can lead to inaccurate, misleading, or even harmful conclusions. Responsible network analysis requires constant awareness and adherence to ethical principles.
Q 14. Describe your experience with different graph database technologies (e.g., Neo4j, Amazon Neptune).
My experience with graph databases extends to both open-source and commercial solutions.
Neo4j: I’ve used Neo4j for building and querying large-scale knowledge graphs. Its Cypher query language allows efficient traversal and analysis of complex relationships. For example, I used Neo4j to build a knowledge graph of scientific publications, enabling the exploration of research trends and collaborations.
Amazon Neptune: I’ve utilized Amazon Neptune for scalable graph database solutions within the AWS ecosystem. Its integration with other AWS services simplifies deployment and management. This was particularly beneficial in a project analyzing a massive social network dataset, where scalability was a primary concern.
My understanding of these technologies includes data modeling, query optimization, and performance tuning. The selection between Neo4j and Amazon Neptune or other similar technologies depends on the project’s specific needs in terms of scalability, cost, and integration with existing infrastructure.
Q 15. How do you choose appropriate visualization methods for different types of networks and data?
Choosing the right visualization method is crucial for effectively communicating insights from network data. The best approach depends heavily on the network’s characteristics (size, type, and properties) and the questions you’re trying to answer. For instance, a small social network might be effectively visualized using a simple node-link diagram, where nodes represent individuals and links represent connections. However, for a large, complex network like the internet, such a representation would be overwhelming and uninterpretable.
For small networks (less than a few hundred nodes): Node-link diagrams are generally suitable, providing a clear view of individual connections. Force-directed layouts are particularly useful for showing community structure.
For large networks: Techniques like matrix visualizations (adjacency matrices showing connections), hierarchical layouts (emphasizing hierarchical relationships), or community detection algorithms followed by visualizing communities separately become necessary. Visualizing only the most important links or nodes (e.g., high-degree nodes) can improve clarity.
For weighted networks (connections with strengths): Edge thickness or color can be used to represent the weight of the connection. For example, in a transportation network, thicker lines might represent highways with higher traffic volume.
For directed networks (connections with directionality): Arrowheads on edges indicate the direction of the relationship. This is essential for visualizing things like information flow or power dynamics.
For specific analysis: Different visualizations highlight different network properties. For example, a circular layout might be helpful for visualizing centrality, while a spatial layout could show geographic proximity in a transportation network.
Ultimately, the choice involves iteratively exploring different visualization techniques until you find one that clearly and effectively communicates the relevant information to your audience.
Career Expert Tips:
- Ace those interviews! Prepare effectively by reviewing the Top 50 Most Common Interview Questions on ResumeGemini.
- Navigate your job search with confidence! Explore a wide range of Career Tips on ResumeGemini. Learn about common challenges and recommendations to overcome them.
- Craft the perfect resume! Master the Art of Resume Writing with ResumeGemini’s guide. Showcase your unique qualifications and achievements effectively.
- Don’t miss out on holiday savings! Build your dream resume with ResumeGemini’s ATS optimized templates.
Q 16. Explain the concept of network motifs and their significance.
Network motifs are recurring, statistically significant subgraphs (small patterns of interconnected nodes) that appear much more frequently in a real-world network than in a random network with the same degree distribution. Think of them as the basic building blocks of network structure. They reveal important functional and organizational principles within the network.
For example, a common motif is a feedforward loop, where node A connects to node B, node B connects to node C, and node A also connects to node C. This motif is often found in gene regulatory networks, where it can act as a signal amplifier or a filter.
The significance of network motifs lies in their ability to:
Reveal underlying network function: Different motifs are associated with different functions. Identifying prevalent motifs can help us understand how the network operates.
Compare networks: Comparing the frequency and types of motifs in different networks can reveal similarities and differences in their structure and function. For example, comparing the motifs of social networks from different cultures might reveal insights into cultural differences.
Generate hypotheses: The discovery of unexpected motifs can lead to new hypotheses about the network’s structure and function. This is particularly useful in biological networks.
Identifying motifs often involves using computational tools to compare the network’s subgraph distribution to a random network’s distribution. Statistical significance testing is essential to distinguish between meaningful motifs and random occurrences.
Q 17. How do you interpret network metrics in the context of a business problem?
Interpreting network metrics in a business context requires understanding how those metrics relate to specific business problems. Let’s consider a few examples:
Degree Centrality: In a customer relationship network, a high-degree customer (connected to many others) might be an influential figure whose satisfaction is crucial for overall business success. Conversely, low-degree customers might be targets for targeted marketing campaigns.
Betweenness Centrality: In a supply chain network, nodes with high betweenness centrality represent critical points of failure. Protecting these points from disruptions is essential for maintaining supply chain resilience.
Closeness Centrality: In a communication network within a company, employees with high closeness centrality can quickly disseminate information, making them valuable for rapid response to urgent situations. Conversely, low closeness centrality could signal information silos.
Eigenvector Centrality: In a social media network, nodes with high eigenvector centrality represent influential individuals, whose opinions could significantly affect brand perception. Targeted marketing efforts towards these influencers are impactful.
Clustering Coefficient: A high clustering coefficient in a collaboration network suggests strong team cohesion and efficient knowledge sharing. A low clustering coefficient could indicate a lack of collaboration and potential information silos.
The key is to link the network metrics to specific business outcomes. For instance, if customer churn is a major concern, analyzing the network structure and the centrality of churning customers can provide insights into the factors driving churn and suggest targeted interventions.
Q 18. Describe your experience with network data cleaning and preprocessing.
Network data cleaning and preprocessing is a crucial step before any analysis or visualization. My experience includes handling various challenges, such as:
Missing Data: Missing edges or nodes are common. I use techniques like imputation (estimating missing values based on existing data) or removal (if the missing data is too extensive). The choice depends on the amount of missing data and the potential impact on the analysis.
Inconsistent Data: Nodes or edges might have inconsistent naming conventions or attributes. I standardize data formats, creating consistent labels and attribute values. This may involve creating controlled vocabularies or using data dictionaries.
Duplicate Data: Removing duplicate nodes or edges, which can distort network statistics, is essential. I employ techniques based on comparing node attributes and edge weights.
Error Correction: Data entry errors can introduce incorrect connections or attribute values. Manual review or automated anomaly detection methods are employed to identify and correct these errors.
Data Transformation: Network data may need transformation to make it suitable for analysis, e.g., converting categorical attributes into numerical representations using one-hot encoding or binary encoding. This could also involve weighting edges based on their importance.
My approach always involves thorough documentation of the cleaning and preprocessing steps to ensure reproducibility and transparency in the analysis.
Q 19. How do you handle dynamic networks (networks that change over time)?
Dynamic networks, which change over time, require specialized handling. Standard static network analysis isn’t sufficient. I typically employ these approaches:
Temporal Network Analysis: This focuses on studying how the network structure evolves over time. It might involve analyzing the emergence, disappearance, and changes in strength of links. Time-series analysis techniques can be used to model the evolution of network characteristics.
Event-Based Modeling: This approach concentrates on the events that cause changes in the network (e.g., new connections forming, connections breaking). Discrete-event simulation is a powerful tool in this context.
Multilayer Networks: Representing the network as a collection of layers, each representing a specific time point or a specific type of relationship, is often effective. This allows for the study of interdependencies between different layers and times.
Visualization Techniques: Dynamic visualizations, such as animated graphs or interactive timelines, are particularly useful for exploring dynamic networks. These let you observe the network evolving in real time.
The choice of approach depends on the nature of the data and the research questions. For example, if you are studying the evolution of a social network, temporal network analysis is appropriate, whereas modeling the spread of a virus might benefit from event-based simulation.
Q 20. What are some common challenges in network visualization?
Common challenges in network visualization include:
Overplotting: In dense networks, nodes and edges can overlap, obscuring the underlying structure. Techniques like edge bundling or using different visual cues (color, size, shape) can mitigate this issue.
Visual Clutter: Excessive detail can make the visualization difficult to understand. Strategies like focusing on a subset of nodes or using hierarchical layouts can help reduce clutter.
Interpretability: Visualizations should be easy to interpret. Clear labeling, legends, and effective use of color and shape are crucial for improving interpretability. Too much visual encoding can lead to confusion.
Scalability: Visualizing very large networks can be computationally challenging. Efficient algorithms and visualization techniques tailored to large datasets are essential. Strategies like sampling or clustering might be necessary.
Choosing the Right Layout: Different layouts highlight different network properties. Selecting the most appropriate layout for the specific data and research question is crucial. Experimentation with several layout algorithms is often needed.
Addressing these challenges requires careful consideration of the dataset, the target audience, and the research questions. An iterative approach, involving experimentation with different techniques and feedback from stakeholders, is essential for producing effective network visualizations.
Q 21. Explain the concept of network embedding and its applications.
Network embedding is a technique that represents nodes in a network as low-dimensional vectors (embeddings) while preserving the network’s structural information. Imagine transforming a complex network into a set of points in a lower-dimensional space, where the proximity of points reflects the relationships between the corresponding nodes in the original network.
This is achieved using machine learning algorithms, often based on dimensionality reduction or deep learning. These algorithms learn to map nodes to vector representations such that nodes with similar network roles or connectivity patterns have similar vector representations.
Applications of network embedding include:
Link Prediction: Predicting missing or future links in a network. Nodes with similar embeddings are likely to be connected.
Node Classification: Classifying nodes into different categories based on their embedding. This is particularly useful in social networks to identify influential users or predict user behavior.
Community Detection: Identifying communities or clusters of nodes based on their embeddings. Nodes within the same community tend to have similar embeddings.
Recommendation Systems: Recommending items or services to users based on their embeddings in a user-item network. Users with similar embeddings are likely to have similar preferences.
Anomaly Detection: Identifying unusual nodes or connections based on their deviation from the expected embedding patterns.
Network embedding offers a powerful way to analyze large and complex networks, enabling the application of machine learning techniques that are not directly applicable to the raw network data.
Q 22. How do you evaluate the quality of a network visualization?
Evaluating the quality of a network visualization hinges on several key aspects. It’s not just about how pretty it looks, but how effectively it communicates the underlying network structure and insights. A good visualization should be both aesthetically pleasing and informative.
- Clarity and Simplicity: The visualization should be easy to understand at a glance. Avoid clutter and unnecessary details. Think of it like a well-written sentence – concise and to the point. For example, using clear node shapes and edge types to represent different categories within the network improves clarity significantly.
- Accuracy and Completeness: The visualization must faithfully represent the data. Missing nodes or edges, or misrepresented relationships, can lead to flawed interpretations. A legend and clear labels are crucial here to ensure everyone understands the visual elements.
- Effectiveness in Communicating Insights: The visualization should help users identify key patterns, structures, and anomalies within the network. For instance, a visualization might highlight the most influential nodes (key players in a social network) or the densest clusters (communities in an online forum). Effective use of color-coding, size variations, and other visual cues greatly enhances insight.
- Scalability: The visualization should remain effective even as the network grows larger. Techniques like hierarchical layouts or force-directed layouts are important for handling large datasets. A poorly designed visualization can become incomprehensible when dealing with hundreds or thousands of nodes and edges.
- Accessibility: The visualization should be accessible to diverse audiences, including those with visual impairments. This includes using appropriate color palettes, sufficient contrast, and providing alternative text descriptions for the visually impaired.
For example, visualizing a social network using a force-directed layout that groups related individuals visually is more informative than simply showing a list of connections. The layout makes it easier to identify communities and central figures within the network.
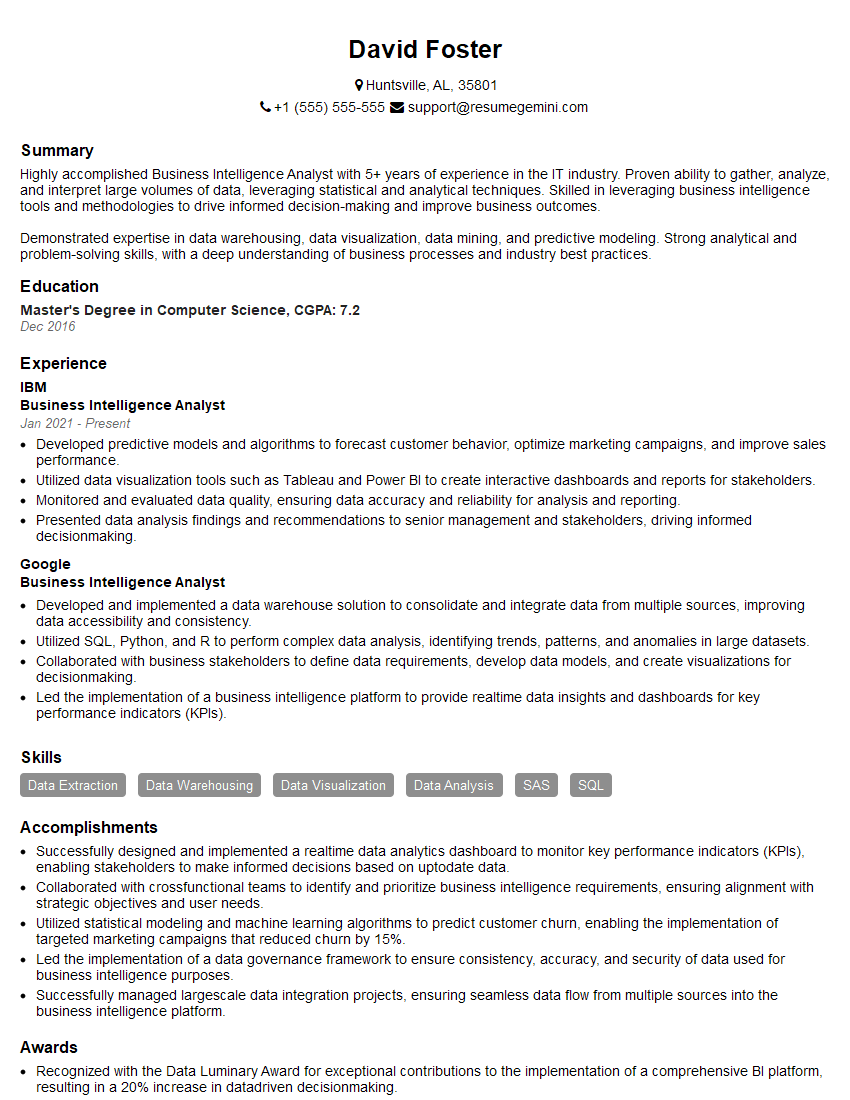
Q 23. Describe your experience with programming languages used in network analysis (e.g., Python, R).
My expertise in network analysis is strongly rooted in Python and R. I’ve extensively used both languages for a variety of tasks, from data cleaning and preprocessing to complex network algorithms and visualization.
- Python: I leverage libraries like
NetworkXfor creating and manipulating network graphs, calculating centrality measures, and running community detection algorithms.matplotlibandseabornare crucial for visualizing the results effectively, whilepandasprovides robust data manipulation capabilities. - R: R’s strength lies in its statistical computing capabilities. Packages like
igraphprovide a comprehensive set of tools for network analysis. I often use R for statistical modeling and hypothesis testing related to network data. Further, visualization in R using packages likeggplot2provides an intuitive approach to generating publication-quality graphics.
For instance, in a recent project analyzing a large email communication network, I used Python’s NetworkX to identify key influencers within the organization based on their centrality measures. Subsequently, I used R’s statistical capabilities to test if the identified influencers had a significant correlation with specific organizational outcomes.
Q 24. Explain how you would approach analyzing a real-world network dataset.
Analyzing a real-world network dataset involves a structured approach. It starts with understanding the context and ends with actionable insights. The process can be broken down into the following steps:
- Data Acquisition and Cleaning: This initial phase involves gathering the data from the relevant sources. The data might be in various formats, requiring cleaning and preprocessing to ensure consistency and accuracy. This may involve handling missing values, standardizing formats, and dealing with errors in the data.
- Network Representation: The data is then converted into a suitable network representation – usually an adjacency matrix or edge list. Choosing the right representation depends on the type of network and the analysis goals. For example, an adjacency matrix works well for representing relationships between nodes, while an edge list may be easier to use for representing large networks.
- Exploratory Data Analysis (EDA): EDA helps uncover initial insights. This includes calculating basic network statistics such as node degree distributions, density, diameter, and clustering coefficients. Visualization plays a key role here, helping to identify major patterns and structures.
- Network Analysis: This is where specific analysis techniques are applied. These might include centrality measures (degree, betweenness, closeness, eigenvector centrality), community detection algorithms, pathfinding algorithms, and various other techniques that will depend on your particular objective. The choice of algorithms depends on the research questions and the type of network under investigation.
- Interpretation and Communication: The final step involves interpreting the results of the analysis. This includes identifying key patterns and trends, understanding the implications of findings and communicating the insights effectively to both technical and non-technical stakeholders. Visualizations are extremely important at this stage to help convey complex information in a clear and accessible manner.
For example, when analyzing a social media network, EDA might reveal the presence of influential users with a high degree of connectivity, which can then be leveraged in marketing strategies. Community detection algorithms could help segment users into groups with similar interests, allowing for targeted advertising and content creation.
Q 25. How do you communicate complex network insights to a non-technical audience?
Communicating complex network insights to a non-technical audience requires careful consideration of the audience’s background and knowledge. The key is to translate technical jargon into plain language and use compelling visuals.
- Analogies and Metaphors: Relate network concepts to everyday examples. For instance, describe centrality measures using analogies like ‘key influencers’ or ‘traffic bottlenecks’ in a transportation network. These simpler comparisons aid understanding.
- Visualizations: Well-designed visualizations are essential. Avoid overwhelming the audience with complex graphs. Instead, focus on clear, easy-to-interpret visuals that highlight the key findings. Consider using interactive visualizations for more engaged understanding.
- Storytelling: Present the findings as a narrative. Start with a clear objective, present the key findings, and explain their significance in a logical sequence. The narrative style makes the information easier to follow.
- Focus on the ‘So What?’: Explain the practical implications of the analysis. How do the findings affect the business, or provide valuable insight into the system being analyzed? Highlighting the practical significance makes the analysis relevant and engaging.
- Interactive Demonstrations: If appropriate, utilize interactive elements, such as clickable maps or charts, to allow non-technical stakeholders to explore the data themselves and discover insights.
For example, instead of saying ‘the network has a high clustering coefficient,’ one might say ‘people tend to form close-knit groups within the network, which is evident in the dense clusters we see in the visualization.’ This simplified explanation is more easily understood by a non-technical audience.
Q 26. What are the limitations of network analysis techniques?
Network analysis, while powerful, has limitations. It’s crucial to be aware of these limitations to avoid misinterpretations and ensure accurate conclusions.
- Data Limitations: Network analysis is highly dependent on the quality and completeness of the data. Missing data, biases in data collection, and errors in the data can significantly affect the results. Inaccurate or incomplete data can skew the analysis and lead to misleading conclusions.
- Model Assumptions: Many network analysis techniques rely on specific assumptions about the network structure and the nature of the relationships. If these assumptions are violated, the results may not be reliable. For example, some algorithms assume a particular type of network structure, whereas in reality the data may not fit this assumption.
- Complexity and Interpretation: Analyzing complex networks can be challenging. Interpreting the results often requires expertise in both network analysis and the specific domain under investigation. Oversimplification or misinterpretation of results can lead to inaccurate conclusions. A lack of appropriate domain knowledge can also impair accurate interpretation of network structures.
- Causality vs. Correlation: Network analysis often reveals correlations between nodes, but it doesn’t necessarily imply causality. Just because two nodes are connected doesn’t mean one causes the other. Further investigation may be needed to establish causal relationships.
- Computational Limitations: Analyzing very large networks can be computationally intensive. Some algorithms may not scale well to massive datasets, limiting their applicability in certain scenarios. The choice of algorithm becomes crucial, weighing computational cost against the desired result.
For example, a study analyzing a social network might find a correlation between two groups of people. However, this correlation doesn’t automatically mean that one group influences the other; it could be due to other unobserved factors. The analysis needs to be careful to avoid implying causality when only correlation is established.
Q 27. Describe your experience with using network analysis for solving business problems.
I have utilized network analysis to solve various business problems. My experience includes applications in areas such as customer relationship management, supply chain optimization, and risk management.
- Customer Relationship Management (CRM): I helped a client analyze their customer network to identify influential customers, understand customer segmentation, and predict churn. By identifying key influencers, targeted marketing campaigns could be implemented more effectively. The analysis of customer connections facilitated personalized marketing initiatives.
- Supply Chain Optimization: I used network analysis to model a company’s supply chain, identifying critical nodes and potential bottlenecks. This allowed for improved inventory management, reduced lead times, and enhanced resilience to supply disruptions. Identifying weak links in the network helped to strengthen resilience within the supply chain.
- Risk Management: I analyzed financial transaction networks to identify potential fraud and assess systemic risk. By identifying anomalous patterns and critical nodes, the company could implement proactive risk mitigation strategies. This facilitated early detection of fraudulent activities and improved control over risks within the financial network.
In each of these scenarios, network analysis provided a deeper understanding of the underlying relationships, leading to data-driven decisions and improved business outcomes. The ability to visualize these complex relationships was crucial in communicating the findings to both technical and non-technical stakeholders.
Key Topics to Learn for Network Analysis and Visualization Interview
- Graph Theory Fundamentals: Understanding nodes, edges, directed/undirected graphs, adjacency matrices, and pathfinding algorithms is crucial. This forms the bedrock of network analysis.
- Network Metrics and Centrality Measures: Learn to calculate and interpret metrics like degree centrality, betweenness centrality, closeness centrality, and eigenvector centrality. Understand their practical applications in identifying influential nodes within a network.
- Community Detection Algorithms: Familiarize yourself with algorithms like Louvain, Girvan-Newman, and label propagation. Be prepared to discuss their strengths, weaknesses, and applicability to different types of networks.
- Network Visualization Techniques: Master various visualization methods, including force-directed layouts, hierarchical layouts, and matrix visualizations. Understand how different visualizations can highlight various aspects of network structure.
- Practical Applications: Prepare examples demonstrating your understanding of network analysis in diverse fields like social network analysis, biological networks, transportation networks, or cybersecurity. Be ready to discuss specific use cases and the challenges involved.
- Data Wrangling and Preprocessing: Network data often requires cleaning and transformation before analysis. Understanding techniques for handling missing data, inconsistencies, and large datasets is vital.
- Software Proficiency: Showcase your skills with relevant software packages like Gephi, NetworkX (Python), igraph (R), or Cytoscape. Be prepared to discuss your experience with these tools.
- Interpreting Results and Communicating Insights: The ability to draw meaningful conclusions from network analysis and communicate them effectively is crucial. Practice explaining your findings clearly and concisely.
Next Steps
Mastering Network Analysis and Visualization opens doors to exciting and impactful careers in data science, research, and various technological fields. To significantly increase your job prospects, crafting a strong, ATS-friendly resume is essential. ResumeGemini is a trusted resource that can help you build a professional resume tailored to highlight your skills and experience effectively. We offer examples of resumes specifically designed for Network Analysis and Visualization professionals to help you showcase your unique qualifications. Take the next step towards your dream career today!
Explore more articles
Users Rating of Our Blogs
Share Your Experience
We value your feedback! Please rate our content and share your thoughts (optional).
What Readers Say About Our Blog
Hello,
we currently offer a complimentary backlink and URL indexing test for search engine optimization professionals.
You can get complimentary indexing credits to test how link discovery works in practice.
No credit card is required and there is no recurring fee.
You can find details here:
https://wikipedia-backlinks.com/indexing/
Regards
NICE RESPONSE TO Q & A
hi
The aim of this message is regarding an unclaimed deposit of a deceased nationale that bears the same name as you. You are not relate to him as there are millions of people answering the names across around the world. But i will use my position to influence the release of the deposit to you for our mutual benefit.
Respond for full details and how to claim the deposit. This is 100% risk free. Send hello to my email id: [email protected]
Luka Chachibaialuka
Hey interviewgemini.com, just wanted to follow up on my last email.
We just launched Call the Monster, an parenting app that lets you summon friendly ‘monsters’ kids actually listen to.
We’re also running a giveaway for everyone who downloads the app. Since it’s brand new, there aren’t many users yet, which means you’ve got a much better chance of winning some great prizes.
You can check it out here: https://bit.ly/callamonsterapp
Or follow us on Instagram: https://www.instagram.com/callamonsterapp
Thanks,
Ryan
CEO – Call the Monster App
Hey interviewgemini.com, I saw your website and love your approach.
I just want this to look like spam email, but want to share something important to you. We just launched Call the Monster, a parenting app that lets you summon friendly ‘monsters’ kids actually listen to.
Parents are loving it for calming chaos before bedtime. Thought you might want to try it: https://bit.ly/callamonsterapp or just follow our fun monster lore on Instagram: https://www.instagram.com/callamonsterapp
Thanks,
Ryan
CEO – Call A Monster APP
To the interviewgemini.com Owner.
Dear interviewgemini.com Webmaster!
Hi interviewgemini.com Webmaster!
Dear interviewgemini.com Webmaster!
excellent
Hello,
We found issues with your domain’s email setup that may be sending your messages to spam or blocking them completely. InboxShield Mini shows you how to fix it in minutes — no tech skills required.
Scan your domain now for details: https://inboxshield-mini.com/
— Adam @ InboxShield Mini
Reply STOP to unsubscribe
Hi, are you owner of interviewgemini.com? What if I told you I could help you find extra time in your schedule, reconnect with leads you didn’t even realize you missed, and bring in more “I want to work with you” conversations, without increasing your ad spend or hiring a full-time employee?
All with a flexible, budget-friendly service that could easily pay for itself. Sounds good?
Would it be nice to jump on a quick 10-minute call so I can show you exactly how we make this work?
Best,
Hapei
Marketing Director
Hey, I know you’re the owner of interviewgemini.com. I’ll be quick.
Fundraising for your business is tough and time-consuming. We make it easier by guaranteeing two private investor meetings each month, for six months. No demos, no pitch events – just direct introductions to active investors matched to your startup.
If youR17;re raising, this could help you build real momentum. Want me to send more info?
Hi, I represent an SEO company that specialises in getting you AI citations and higher rankings on Google. I’d like to offer you a 100% free SEO audit for your website. Would you be interested?
Hi, I represent an SEO company that specialises in getting you AI citations and higher rankings on Google. I’d like to offer you a 100% free SEO audit for your website. Would you be interested?
good